Tech and Gadgets
How to Watch NBA Live Free Using Streaming Sites
The best way to watch NBA live free is by using reliable free NBA live streaming sites that legally share links, trial-based platforms, or official free access windows, while protecting…
Is SEO still relevant in 2026?
Search behaviour has changed significantly over the last few years, but SEO remains a core part of how people discover businesses online. While algorithms are more advanced and user expectations…
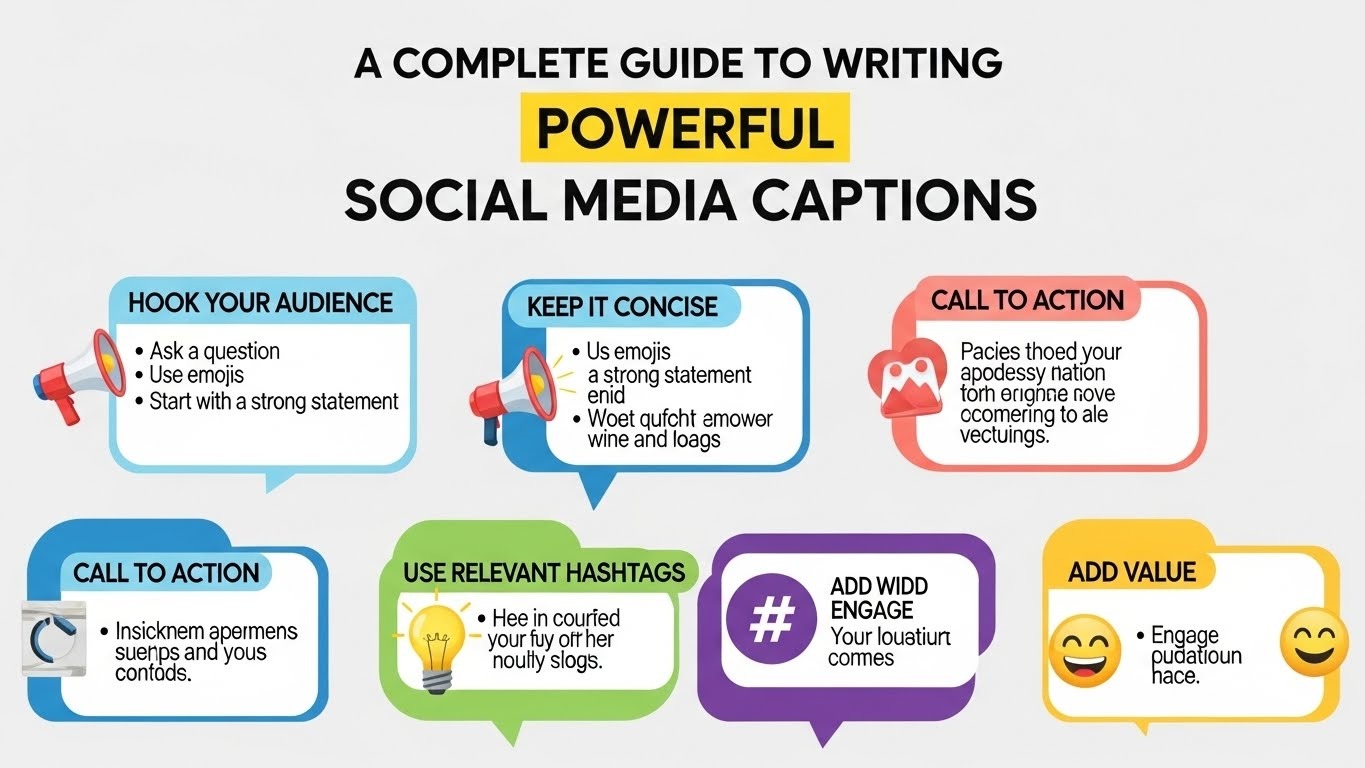
A Complete Guide to Writing Powerful Social Media Captions
What Are Social Media Captions and Why Do They Matter? Short answer: Social media captions are the text that accompanies a post and explains, persuades, or prompts action. They directly…
Stunning Instagram Feeds That Redefine Visual Storytelling
What are stunning Instagram feeds and why do they matter today? Short answer: Stunning Instagram feeds are profiles that use consistent visuals, storytelling, and intentional design to communicate a clear…
Business
Food and Bevarage
Travel
Fashion
Recent Posts
Categories
Trending Posts
Industrial Ironing Equipment and Industrial Washing Machines: Complete Solutions for Commercial Laundry
Imagine transforming your commercial laundry operation from a chaotic, time-consuming chore into a streamlined powerhouse of efficiency. Businesses like hotels, hospitals, and laundromats handle massive volumes of linens daily. They…
How rising costs have led to growth in the litigation funding market
UK businesses are thinking harder before taking a dispute to court. With solicitor and counsel fees, expert evidence, disclosure obligations and lengthy timetables, the overall cost of litigation can escalate…
Dash Mini Rice Cooker: Features, Pros, Cons and Real User Experience
Imagine whipping up perfect rice in a tiny kitchen without hassle. The Dash Mini Rice Cooker changes that dream into reality for many home cooks. This compact device fits small…
Four benefits of hiring a virtual assistant
Businesses are exploring support models that allow them to scale without committing to permanent staff. One option is the use of remote administrative professionals, who can provide structured assistance while…
KitchenAid 3-Piece Pasta Roller And Cutter Set Review: Is It Worth It?
Introduction: Elevate Your Pasta Game at Home There’s something magical about fresh, homemade pasta. The silky texture, the rich flavor, and the satisfaction of creating it from scratch make it…
Box vs Clam Reel: Which One Prevents Line Tangles?
Picture this. You stand by the lake at dawn, rod in hand, ready for a perfect cast. Suddenly, your line twists into a knotty mess. Frustration builds. Line tangles ruin…